自己做完一輪後發現有很多Authentication和Authorization知識和觀念需要再補強: OAuth Flow、OpenID Connect、User federation、憑證的SAN。或許之後會在整理一篇比較偏觀念性的,並且可以對照這一篇出現的概念。
此外,Keycloak感覺十分強大,可以整合很多服務,值得進一步研究
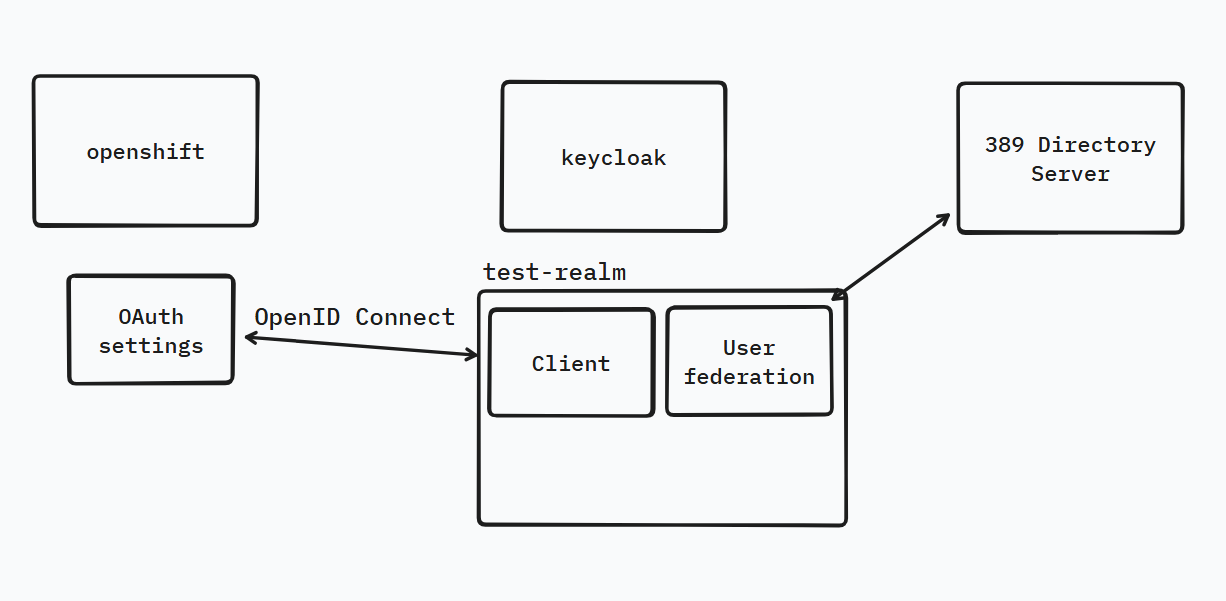
目標
使用389 Directory Server的帳號與密碼登入Openshift Console
前置作業
- Openshift 4.17
- Ingress URI: apps.foo.bar.com
- Keycloak 22.0.4
- 啟用HTTPS且憑證需要包含SAN(Subject Alternative Name)
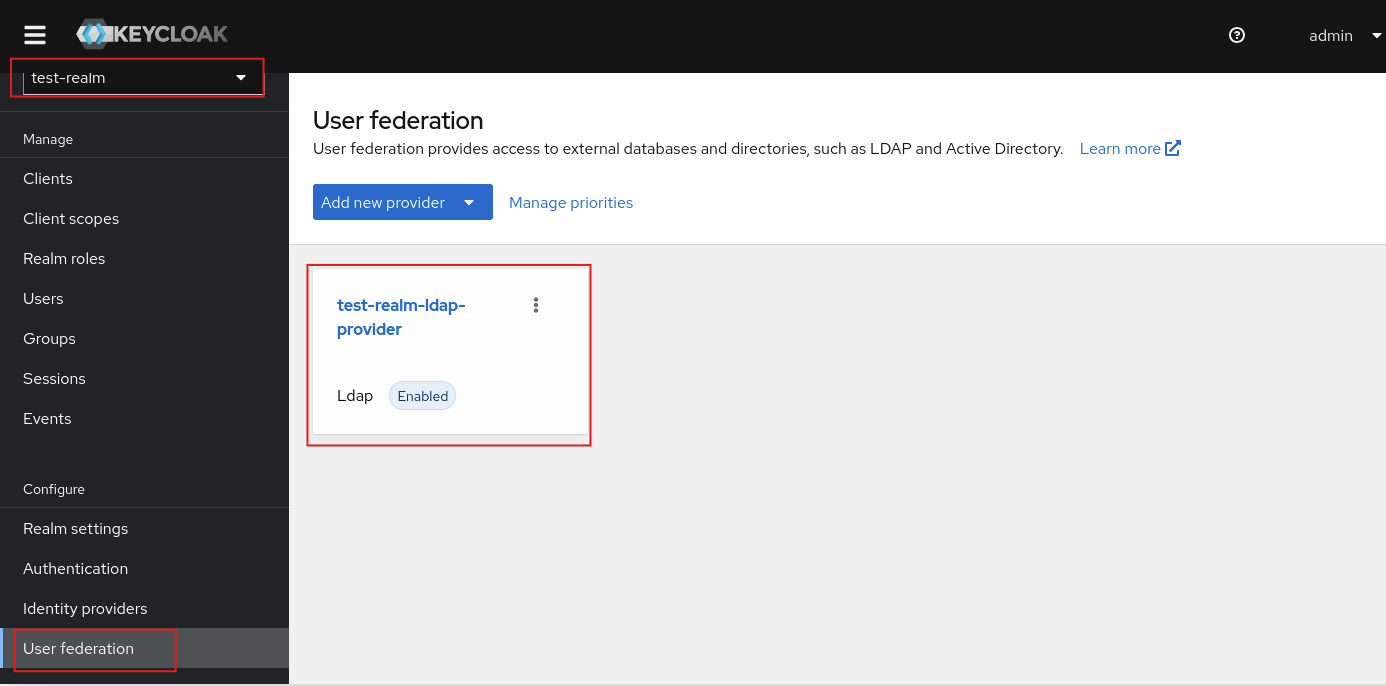
- User federation設定介接389 Directory Server
- DNS有一筆FQDN: keycloak.bar.com
啟用HTTPS且憑證需要包含SAN(Subject Alternative Name)
參考這篇,Keycloak container啟用HTTPS
User federation設定介接389 Directory Server
使用slominskir/keycloak_ldap: Docker Compose with Keycloak and 389 LDAP Directory Server當作例子
啟動container後預設Realm會有test-realm,包含一位使用者jdoe,User federation存在一個設定test-realm-ldap-provider
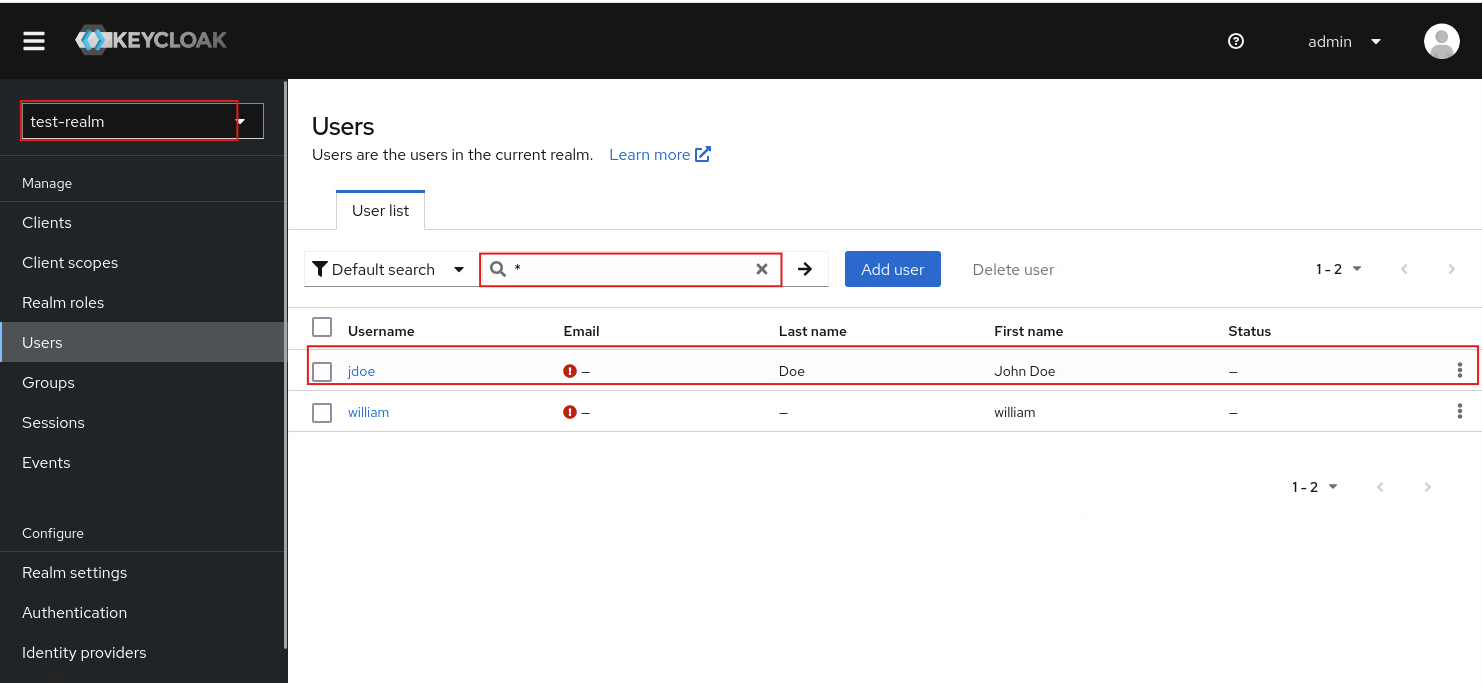
這位預設的使用者並無指定密碼,可以進入至ldap的container內設定
1 | dsidm localhost account reset_password uid=jdoe,ou=People,dc=example,dc=com |
主要設定
- Keycloak Client
- Openshift OAuth settings
Keycloak Client
在Keycloak端的設定新增一個Client
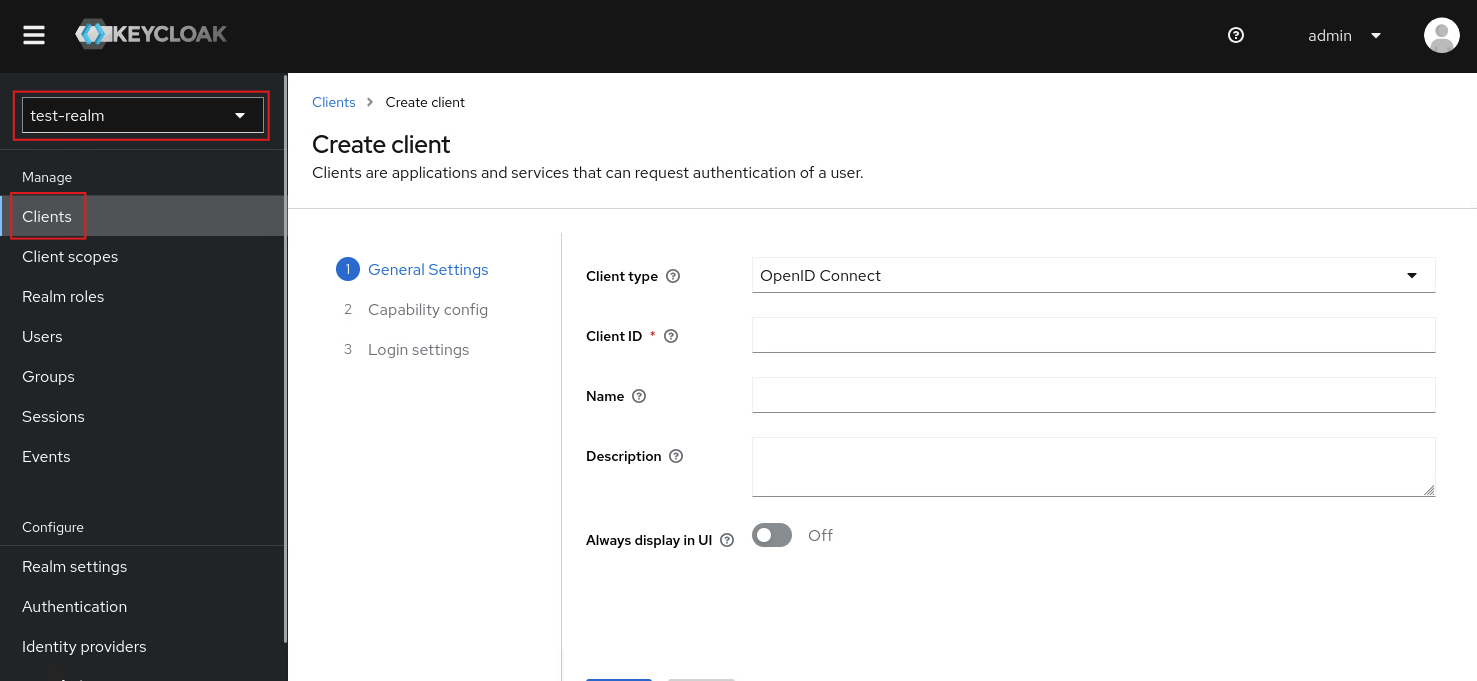
- Client type:
OpenID Connect - Client ID:
keycloak
須注意這邊的keycloak可以設定其他任意值,需要和後續Openshfit內的設定有關
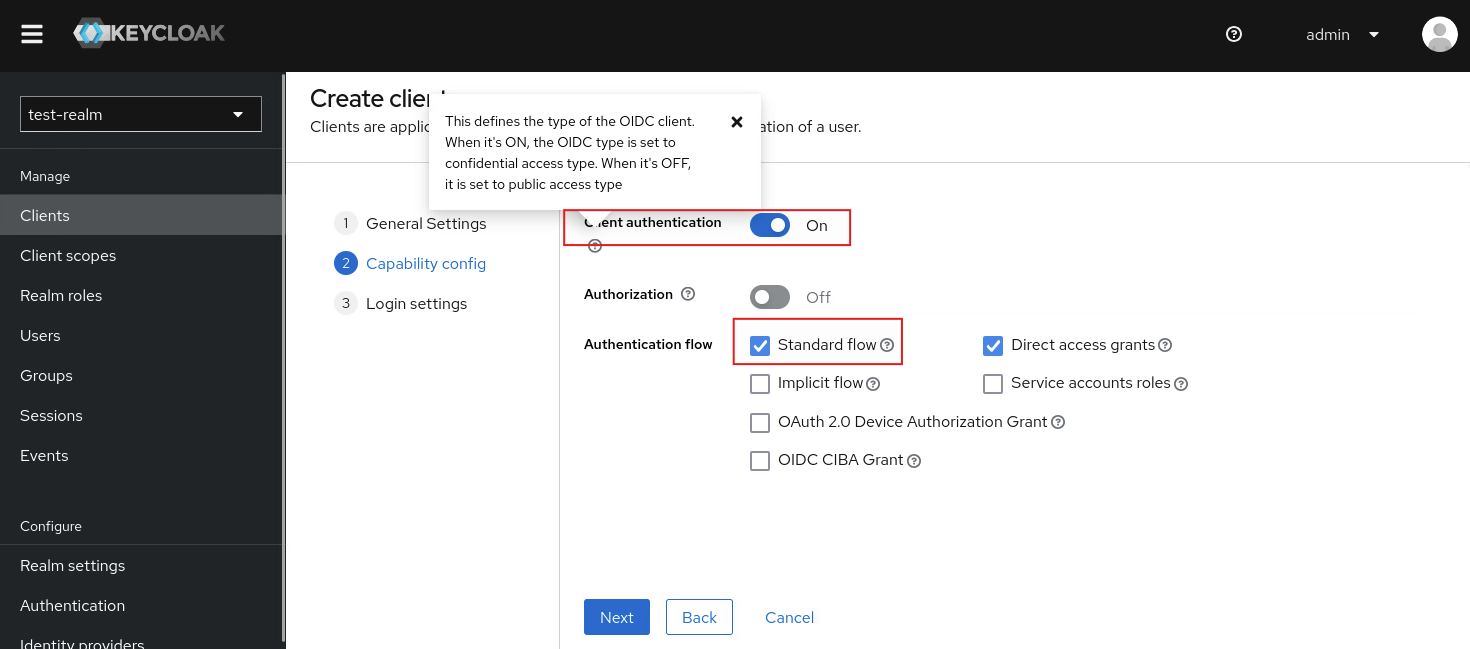
- Client authentication:
On - Authentication flow:
Standard flow
詳細說明可參考保哥的如何用 Docker 快速上手 Keycloak 開發模式
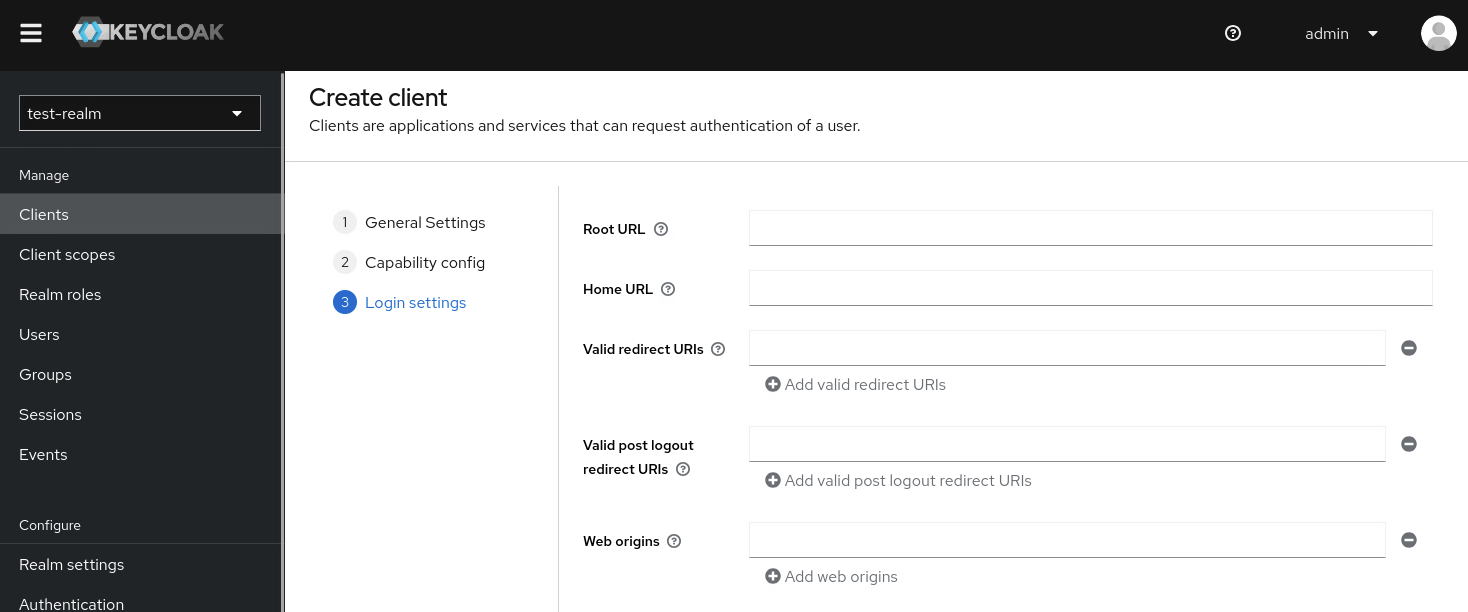
- Valid redirect URIs: https://oauth-openshift.apps.foo.bar.com/oauth2callback/openid
須注意最後面的openid字串可以設定其他任意值,需要和後續Openshfit內的設定有關
Openshift OAuth settings
Adminitration => Cluster Settings => Configuration => OAuth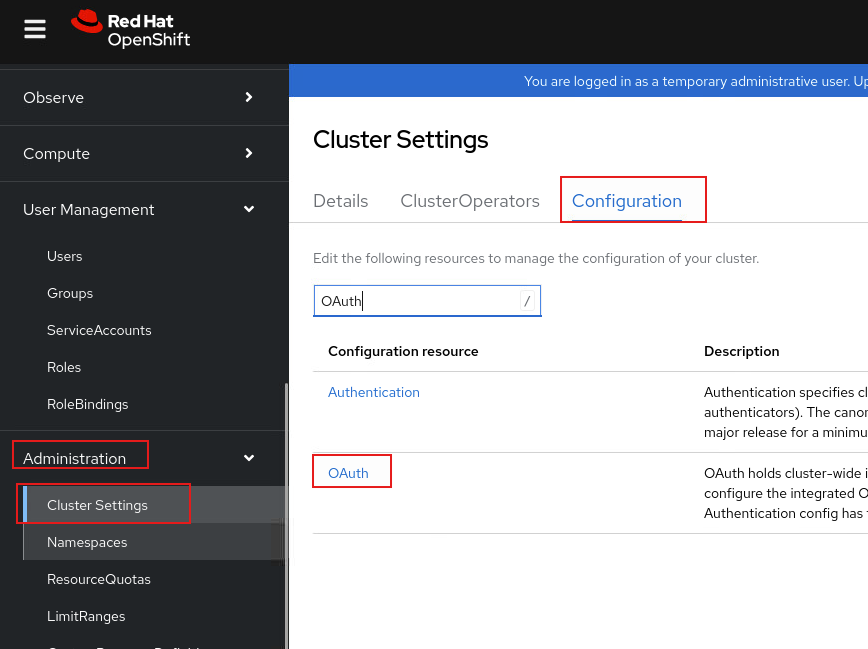
Identitiy providers => Add ‘OpenID Connect’
- Name:
openid- 和Keycloak Client的Valid redirect URIs有關
- Client ID:
keycloak- 和Keycloak Client的Client ID有關
- Client secret: 可以在Keycloak Client的Credentials找到
- Issuer URL:
https://keycloak.bar.com:8443/realms/test-realm- test-realm是Keycloak內的Realm
- 需要HTTPS
- 這邊需要注意Keycloak的版本的URI會有些差異,可以參考Keycloak: All API response with 404 - Stack Overflow,版本17(包含)之後的URI沒有auth的字串https://keycloak.bar.com:8443/realms/yourrealm,版本17(不包含)之前的URI有auth的字串,http://keycloak.bar.com:8443/auth/realms/yourrealm
- CA file
- Keycloak的憑證,需要包含SAN(Subject Alternative Name)
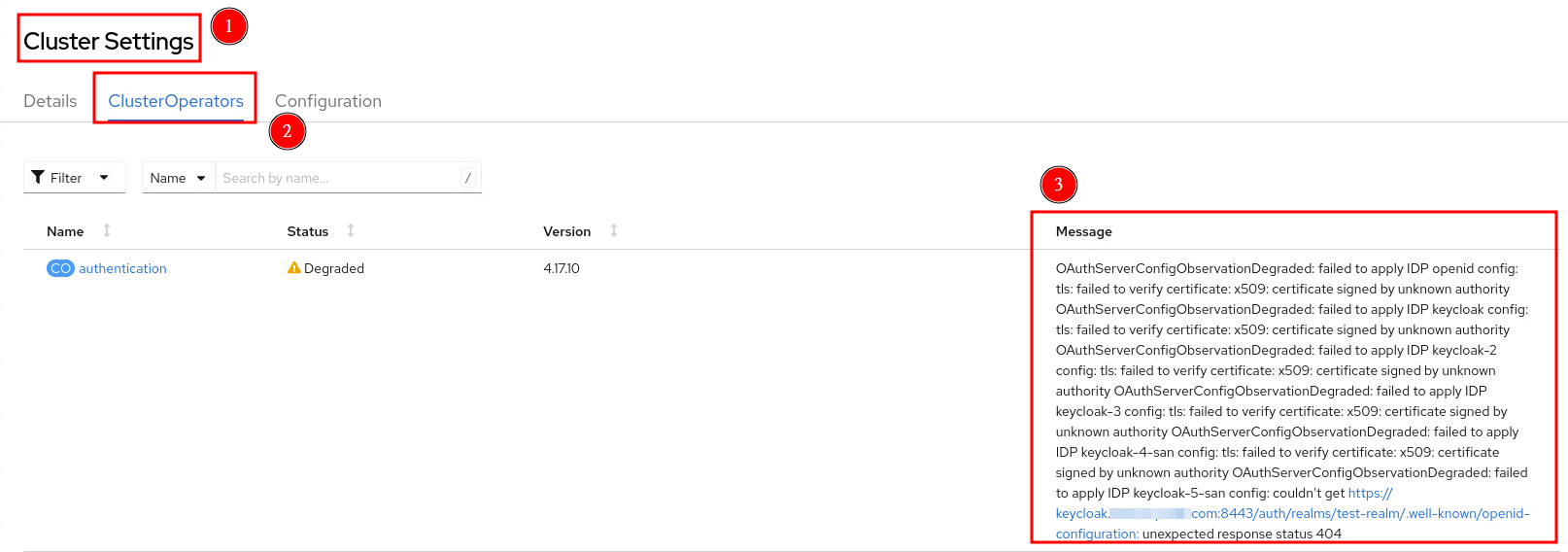
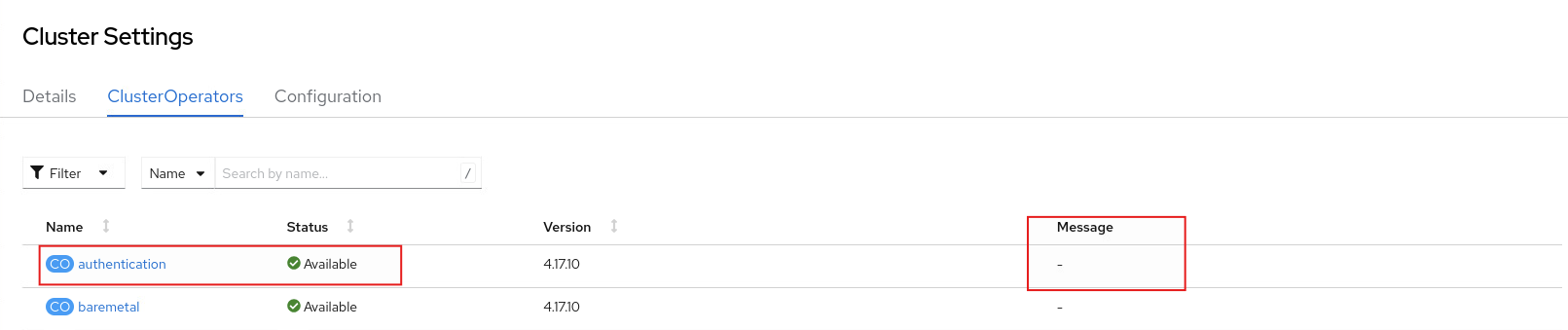
有發生錯誤的話可以在Cluster Settings的ClusterOperators中關於authentication的Message看到相關訊息,有遇到以下幾個狀況
- 憑證不包含SAN時,會出現OAuthServerConfigObservationDegraded: failed to apply IDP openid config: tls: failed to verify certificate: x509: certificate relies on legacy Common Name field, use SANs instead
- Issure URL有問題,有出現well-known/openid-configuration:
例如下圖
成功的話Status顯示Available且登入畫面會出現所設定的OpenID Connect
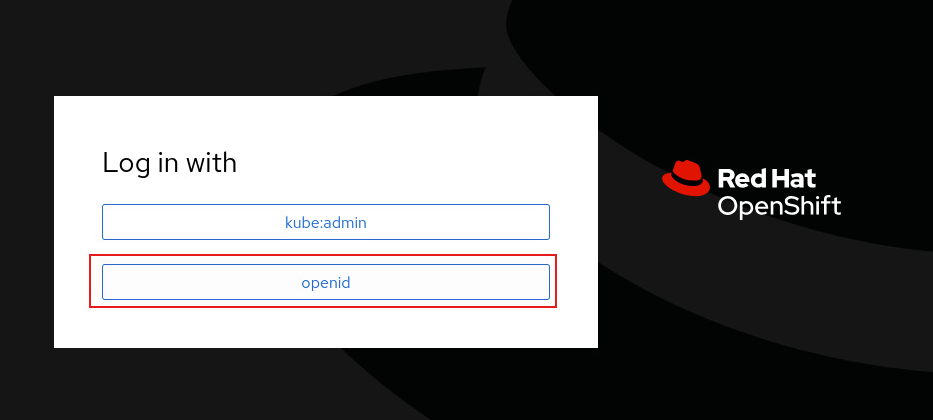
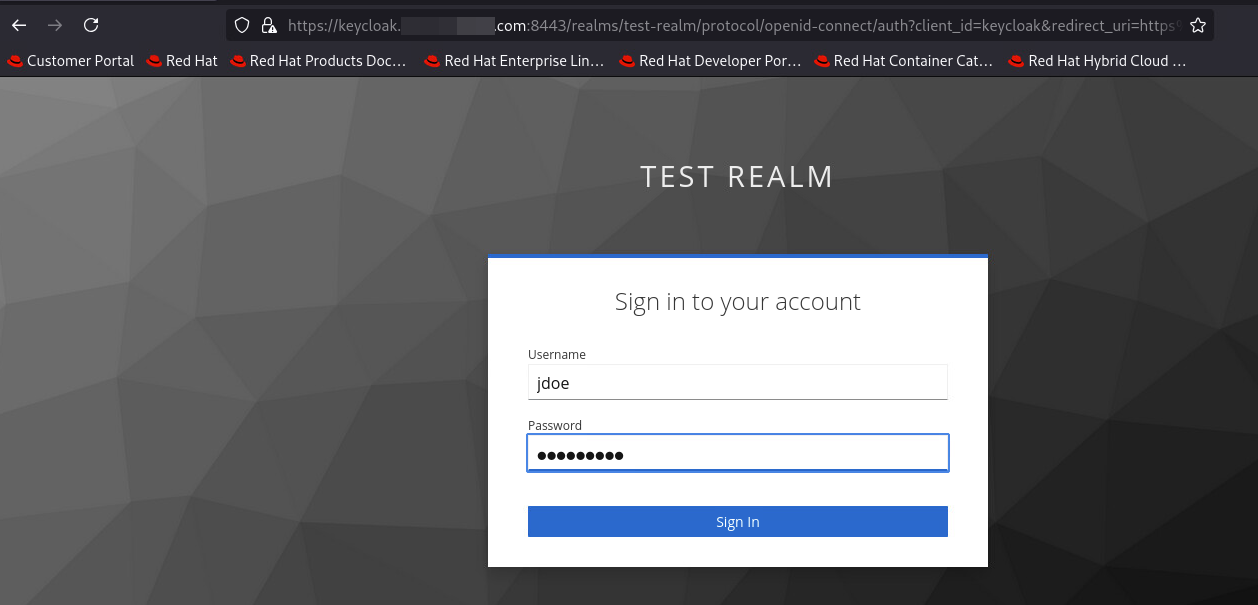
測試
有client_id和redirect_uri,看起來是之前在Keycloak Client當中設定的值
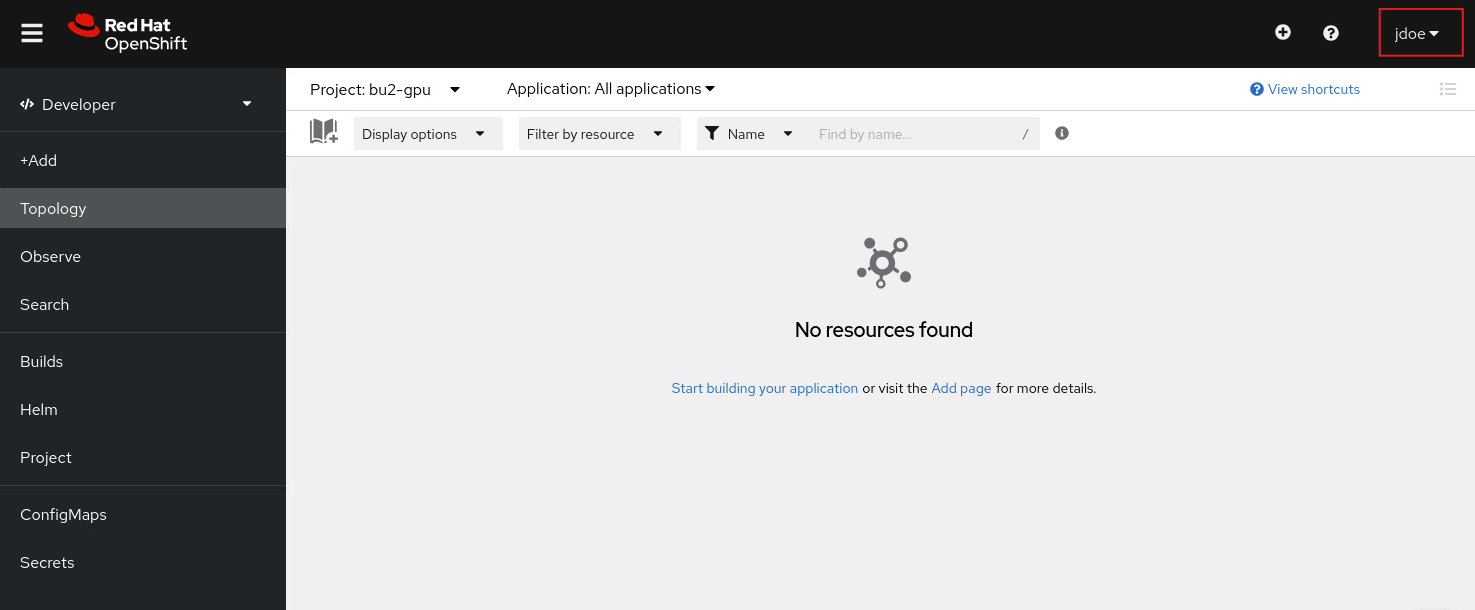
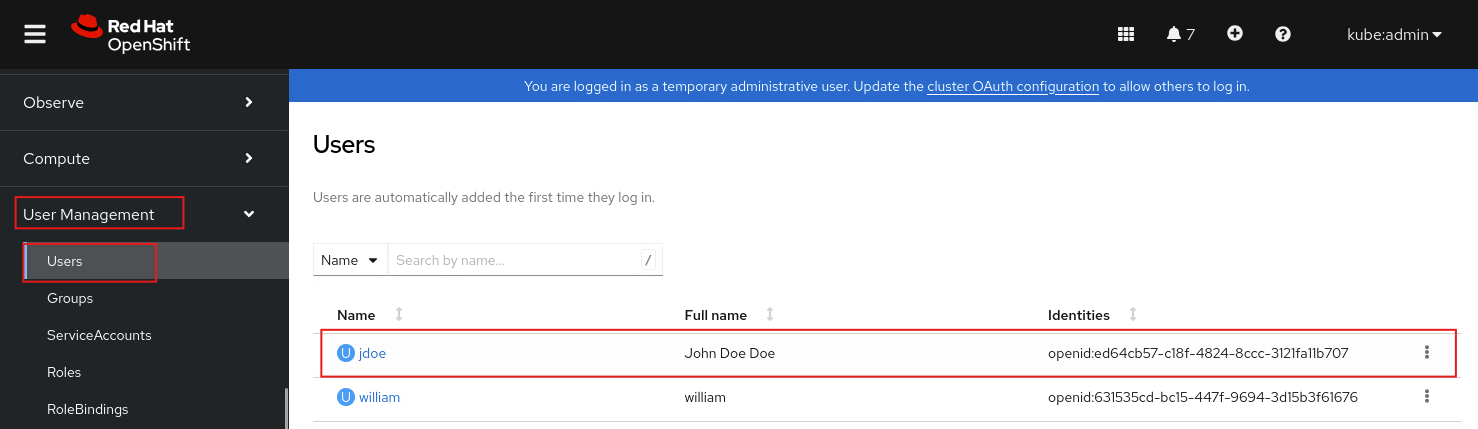
可以在kubeadmin觀察,jdoe登入後在User Management => Users會出現一筆紀錄,Identities為openid:xxx
參考
- OpenShift, SSO with KeyCloak & Active Directory | DELL Technologies
- How to Integrate OpenShift with Keycloak - The New Stack
- LDAP
- 憑證
- Error x509: certificate relies on legacy Common Name field, use SANs instead in Openshift - Red Hat Customer Portal
- How to create custom self-signed certificates for ingress and apiserver for Openshift using openssl - Red Hat Customer Portal
- How to create a certificate with Subject Alternative Name (SAN) extensions for OpenShift 4 mirror registry - Red Hat Customer Portal
- Create a self-signed certificate using OpenSSL | by Allan Sun | 隨筆雜記
- 用 SAN Certificate 做 Multi-Domain Certificate | by Allan Sun | 隨筆雜記
- “Could not create user” : Error when trying to log in to Red Hat OpenShift console - Red Hat Customer Portal